Remote SSH For IoT Devices: Trends, Examples & Security
Is the future of the Internet of Things (IoT) secured, or are we overlooking critical vulnerabilities? Remote Secure Shell (SSH) access to IoT devices isn't just a convenience; it's becoming an absolute necessity for efficient management, yet its implementation carries significant security implications that demand careful consideration.
As the world becomes increasingly interconnected, with billions of devices communicating and exchanging data, the role of remote SSH access in the IoT ecosystem continues to evolve. The ability to securely connect to and manage devices from afar is no longer a luxury but a fundamental requirement for maintaining functionality, security, and efficiency. This article delves into the future trends, practical applications, and critical considerations surrounding SSH in the context of IoT. It explores how developers and administrators can harness the power of SSH to ensure robust security and seamless device management, even in the face of growing cyber threats.
One of the primary trends shaping the future of IoT device remote SSH is the increasing reliance on cloud platforms. Companies are leveraging services like Amazon Web Services (AWS) and Microsoft Azure to streamline remote management processes. This integration allows for more centralized control, automated updates, and improved security monitoring. These cloud platforms offer a range of tools and services that simplify the setup and maintenance of SSH connections, making them more accessible and manageable at scale. By integrating SSH with these services, developers can easily establish secure tunnels, manage user access, and monitor device activity, enhancing the overall security posture of their IoT deployments.
Let's delve deeper into the specifics of how SSH works within the IoT and how it will shape the future. We will explore the intricacies of setting up SSH on your IoT device to troubleshooting common issues, and provide practical examples and best practices to ensure that your remote connections are both secure and efficient. We will navigate everything from the initial configuration of the SSH server to advanced security measures, such as key-based authentication and firewall configurations.
Heres a breakdown of the key aspects of setting up and securing remote SSH access to your IoT devices. We'll cover essential steps like enabling SSH, configuring the server, securing the connection, and practical methods for troubleshooting common problems.
Implementing secure remote access is crucial for maintaining strong cybersecurity in the evolving landscape of the Internet of Things. As more and more devices connect, ensuring the security of these connections becomes critical to prevent unauthorized access, data breaches, and other malicious activities. Understanding how to properly implement and manage SSH connections is essential for anyone involved in the development, deployment, or maintenance of IoT devices. Here are some critical points to ponder, which will provide you with a comprehensive understanding of how to implement secure remote access.
| Topic | Details |
|---|---|
| Future Trends |
|
| Key Technologies |
|
| Security Best Practices |
|
| Use Cases |
|
| Troubleshooting |
|
Reference: Example Website
Setting up an SSH tunnel to a Raspberry Pi or other IoT device can be a straightforward process with the right knowledge. While the specifics vary slightly depending on the device and network configuration, the general steps remain the same. A key aspect of secure remote SSH access involves the proper configuration of firewalls. Firewalls are often used to protect IoT devices, but they can also complicate remote access.
To start, you'll need to enable SSH on your IoT device. Most IoT devices run on lightweight operating systems such as Linux and may have SSH disabled by default for security reasons. To enable it, you will need to install an SSH server on the device if it's not already present. This typically involves installing an SSH daemon.
With the SSH server running, youll then need to configure the firewall settings to allow inbound SSH connections. This usually means opening port 22 (the default SSH port) or another custom port that you may have configured. Ensure that you have a strong password for your SSH account or, preferably, set up key-based authentication for enhanced security.
Once your SSH server is set up and your firewall is configured, you can test the connection from a remote machine. Open an SSH client, such as PuTTY or the SSH command-line tool, and connect to your IoT device using its IP address and the configured port. Authenticate with your username and password or your SSH key, and if everything is set up correctly, you should be able to access the device's command line.
Remote IoT device management becomes especially useful when your IoT devices are deployed in situations that are physically dangerous or challenging to reach, such as in remote locations, hazardous environments, or areas with limited accessibility. This reduces the necessity for on-site technicians, therefore reducing costs and increasing efficiency.
One of the key advantages of SSH is its ability to create secure tunnels. SSH tunnels encrypt all the data transmitted between the client and the server, making it extremely difficult for attackers to intercept and read the data. This is particularly crucial when transmitting sensitive information, such as device configurations, user credentials, and sensor readings. Another critical element is the use of key-based authentication. Instead of relying on passwords, which can be vulnerable to brute-force attacks and phishing attempts, SSH key-based authentication uses cryptographic keys to verify the identity of the user. This is significantly more secure and is highly recommended for IoT deployments.
One common method of securing access is through the use of firewalls, which are designed to block unauthorized access to devices. Firewalls are often configured to block all inbound traffic to the device, which can make it difficult to establish a direct SSH session. However, by creating an SSH tunnel, you can bypass the firewall and establish a secure connection. To accomplish this, you'll typically need to configure your firewall to allow outbound traffic on port 443 (or the port your tunnel uses). This will enable your device to connect to a server or service that can then relay the SSH traffic to your device.
There are several tools and platforms that facilitate remote SSH access to IoT devices. Some of the popular choices include:
- SocketXP: SocketXP offers a scalable solution for remote SSH access. It provides an agent that can be installed on your IoT device, allowing you to establish an SSH tunnel through their platform without the need to discover the device's IP address or change firewall settings.
- AWS IoT: AWS IoT can be integrated with SSH to provide secure remote management capabilities.
- Azure IoT Hub: Azure IoT Hub offers similar features as AWS IoT.
- OpenSSH: A widely used open-source SSH implementation that can be installed and configured on most Linux-based IoT devices.
Implementing these security measures will greatly enhance the overall security of your IoT devices and networks.
To SSH into your IoT device, use the SSH command along with the public URL and port number obtained in the previous step. Replace "username" with the username of your IoT device. A sample command may look something like this: ssh username@public_url -p 40527
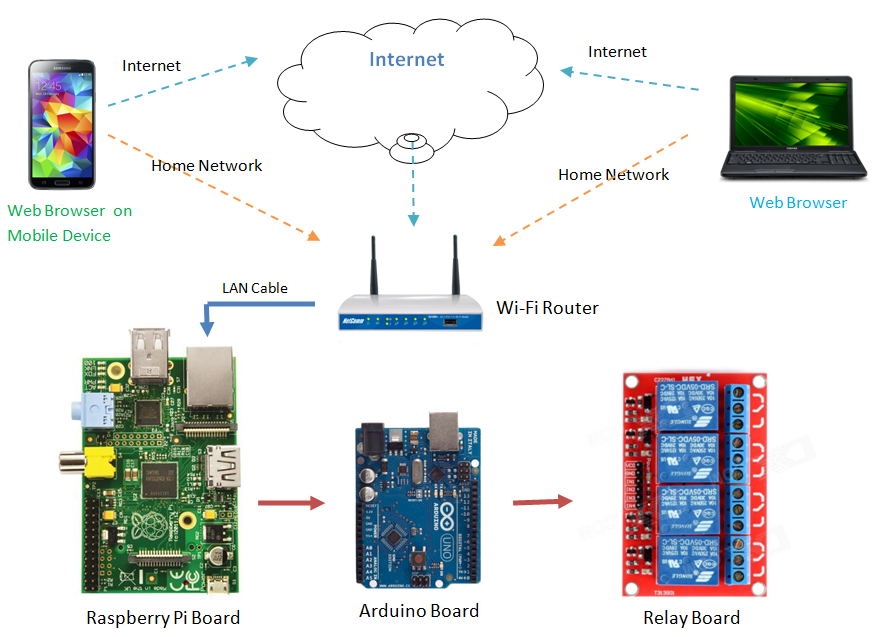
The remote IoT platform allows users to remotely control IoT devices using a web browser. This approach simplifies device management and enhances accessibility. This is often achieved by setting up a VNC server on a device like a Raspberry Pi. A VNC client application on a device of your choice can then be used to view and interact with the Pi's desktop from anywhere with an internet connection, providing a comprehensive control interface.
In conclusion, remote SSH access is a critical component of modern IoT systems, empowering secure device management and control. By understanding the trends, implementing security best practices, and leveraging tools like cloud platforms and SSH tunnels, developers and administrators can create robust and secure IoT environments. As IoT continues to evolve, the importance of secure remote access will only increase, making it essential for anyone involved in the world of connected devices.